SpotMon
Identify Bad Actors & Slackers in Salesforce
The turnkey solution for Shield Event Monitoring
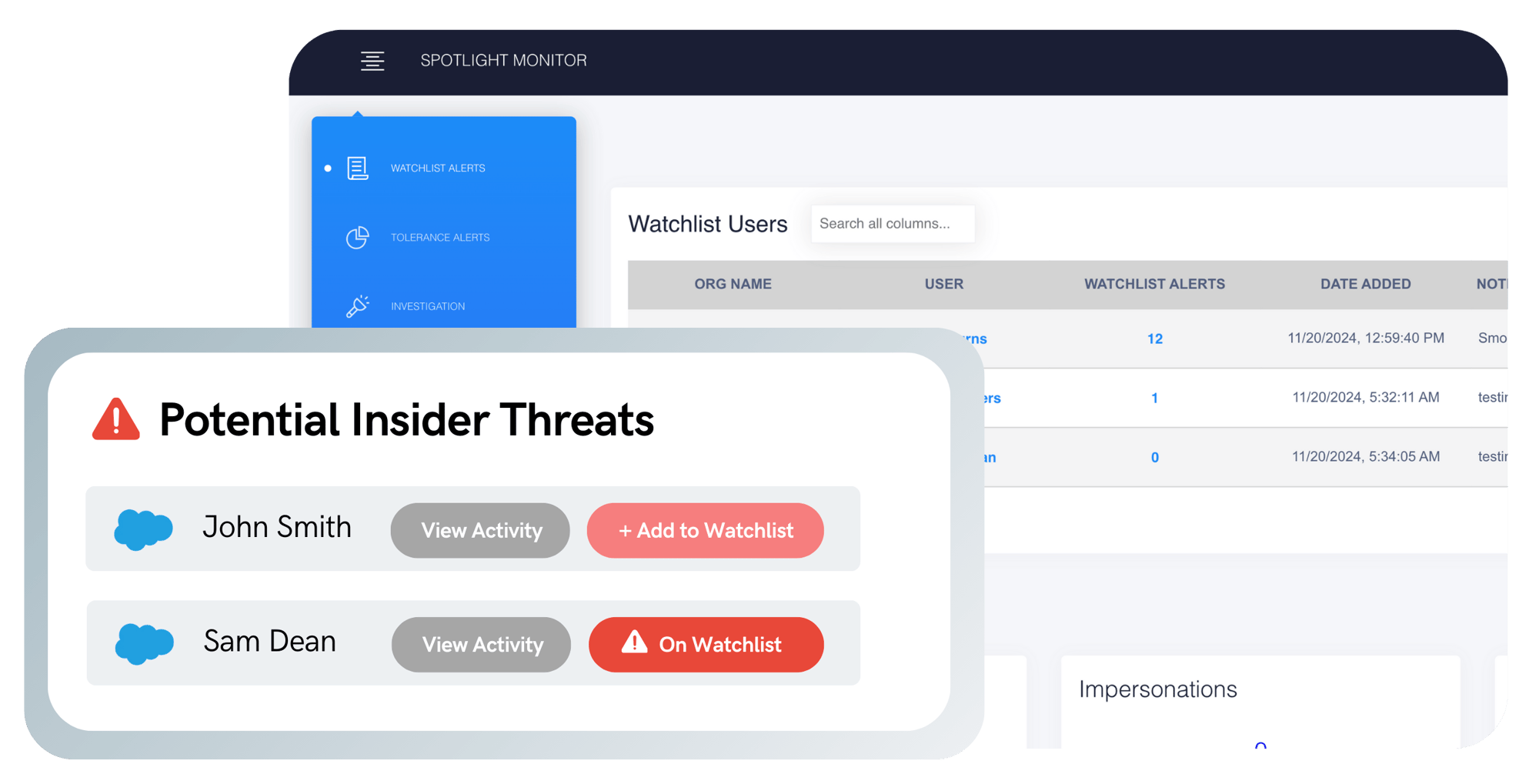
Key questions SpotMon answers for...
How SpotMon works
1. Automatically generated tolerance levels
Tolerance levels are auto generated based on your company's user behavior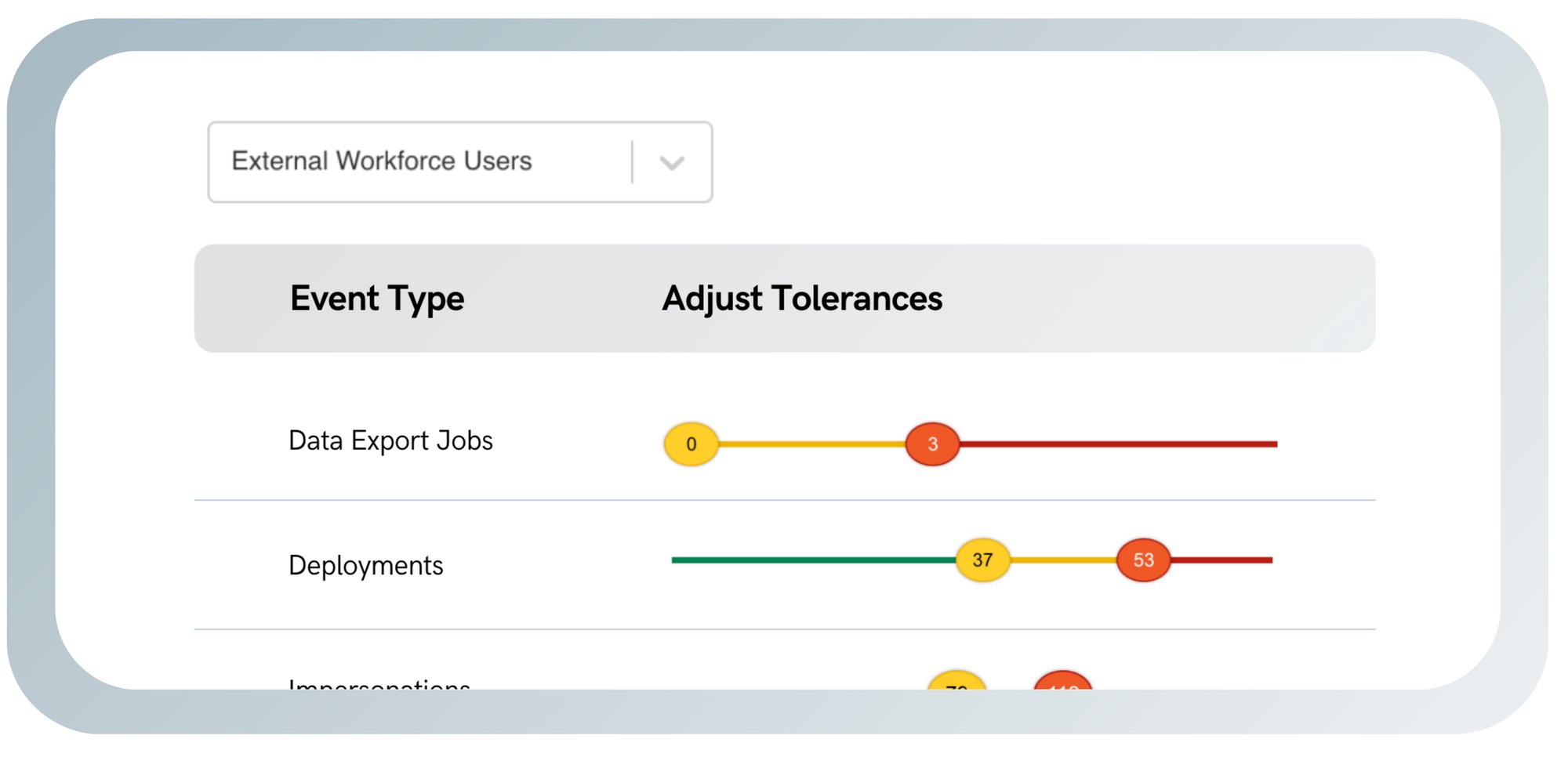

2. Monitor suspicious user activity
Get real-time alerts for highly unusual or suspicious activities
3. Investigate & take action
Pinpoint the exact nature of suspicious activities.png)
Why SpotMon
-
60% of data breaches are from internal users
-
SpotMon is a turnkey solution for Salesforce Event Monitoring and investigating Salesforce user activity
-
Built by Salesforce Shield experts
- Purpose built for small and mid-market customers
